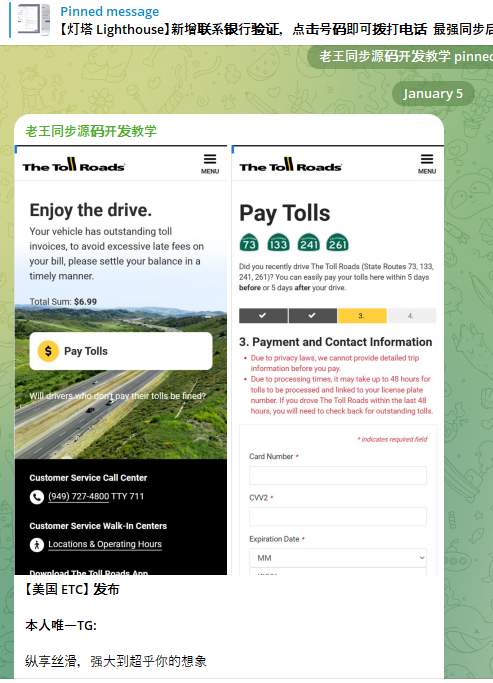
1,000+ Servers Hit in Law Enforcement Takedown of Rhadamanthys, VenomRAT, Elysium
An individual believed to have been involved in the operation of VenomRAT was arrested recently in Greece. The post 1,000+ Servers Hit in Law Enforcement Takedown of Rhadamanthys, VenomRAT, Elysium appeared first on SecurityWeek.